The Risks that Hong Kong Businesses Must Not Ignore
For many decision-makers in Hong Kong SMEs, photocopiers are still regarded as simple office devices used only for printing and scanning documents, with little perceived security risk. However, as photocopiers become increasingly intelligent—capable of connecting to internal networks, cloud systems, and storing large volumes of business documents—photocopier security has become one of the most overlooked elements in corporate information security.
Without proper antivirus protection and security management, a company photocopier can easily become a vulnerability exploited by hackers to infiltrate the corporate network. This may result in confidential document leakage, disruption to order or business systems, or even network breaches that go unnoticed. For Hong Kong enterprises handling contracts, financial records, and customer data daily, such incidents can lead not only to privacy exposure but also long-term operational and reputational damage.
Within corporate IT infrastructure, firewalls, endpoint antivirus software, and server security are typically prioritised, while photocopiers are often excluded from formal information security management. This is largely because photocopiers have long been viewed as “paper-based equipment” rather than network-connected devices capable of storing corporate data.
In reality, modern multifunction photocopiers operate with independent operating systems, IP addresses, and constant connections to corporate intranets. Without proper antivirus mechanisms, access controls, and regular updates, their risk level is no different from an unprotected computer—making them a common entry point for photocopier hacking incidents.
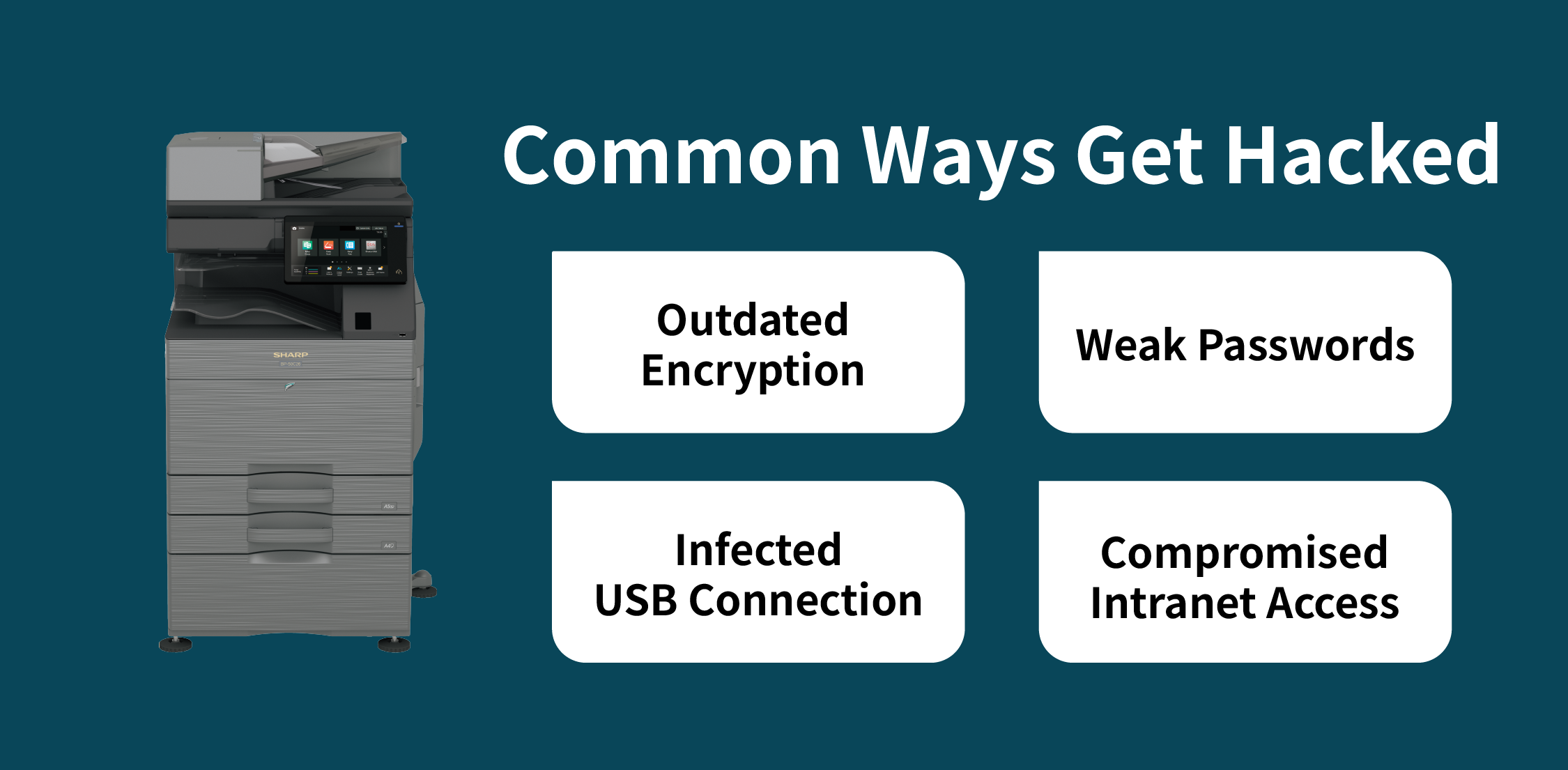
In many cases, photocopier hacking does not stem from sophisticated cyberattacks but from preventable day-to-day security oversights.
If print and scan data is transmitted over the network without encryption, it may be intercepted—especially when handling contracts, financial documents, or personal data.
Photocopiers using factory default settings or lacking user authentication can allow unauthorised access to system configurations.
While USB printing and scanning offer convenience, they can also serve as entry points for malware, compromising overall photocopier security.
Once a photocopier is compromised, attackers may exploit its network privileges to move laterally across internal systems, expanding the scope of the breach.
Photocopiers often store large volumes of scanned and printed data. A breach can expose sensitive information and lead to legal and regulatory consequences.
If used as a malware entry point, the impact may extend beyond a single device to the entire office network.
Post-incident system recovery, data restoration, and IT support costs often far exceed the investment required for preventive photocopier security measures.
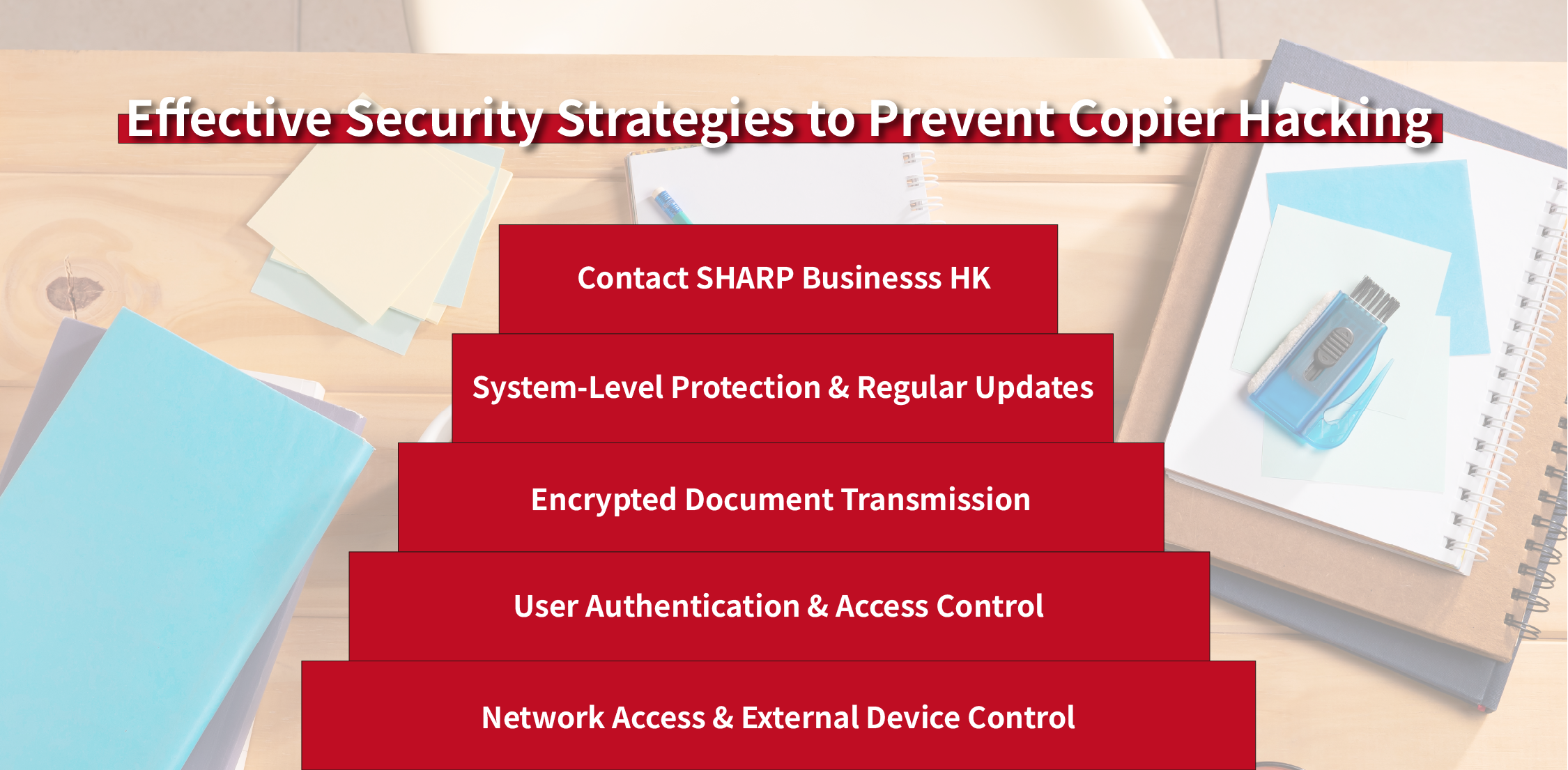
Truly effective photocopier antivirus protection is not a single feature, but a multi-layered defence strategy:
• System-level protection and regular firmware updates
• Encrypted document transmission and storage
• User authentication and access control
• External device and network access management
These measures together form a comprehensive photocopier security framework.

The following industries handle large volumes of documents and sensitive data, making photocopier security especially critical:
• Financial and professional services
• Healthcare and clinics
• Educational institutions
• SMEs and multi-department offices
Wherever sensitive documents are involved, photocopier security cannot be ignored.

Businesses should begin at the equipment selection stage, ensuring photocopiers are designed with enterprise-grade security, supported by clear internal usage policies and regular reviews.
By combining governance and technology, photocopier security can evolve alongside business growth—rather than becoming a one-time configuration that is eventually neglected.

SHARP Business HK provides security-focused photocopier and document management solutions for Hong Kong enterprises, helping businesses:
• Integrate photocopiers into overall information security frameworks
• Strengthen document access and management controls
• Align with local office workflows and compliance requirements
• Receive professional technical support and security consultancy
If you wish to enhance photocopier security and document protection without disrupting daily operations, SHARP Business HK can deliver tailored recommendations and solution assessments based on your business needs.
Yes. As long as a photocopier is connected to the corporate network, stores data, and lacks proper security management, it carries real hacking risks. Many organisations are now recognising the data breach and cybersecurity threats associated with compromised photocopiers.
Photocopier antivirus protection extends beyond software installation. It includes system protection, access control, data encryption, and secure configuration. For businesses, it should form part of an integrated photocopier security strategy.
A compromised photocopier can lead to confidential data leakage, network intrusion, and even act as a gateway for ransomware attacks—causing long-term operational and reputational damage.
Yes. SMEs also handle customer data, contracts, and internal documents. Insufficient photocopier security can pose risks comparable to those faced by larger enterprises.
Basic security settings are usually included in photocopier rental services. However, businesses should further tailor security and antivirus configurations according to their IT policies and usage scenarios.
Check whether default passwords are still in use, whether unauthorised USB access is allowed, and whether system updates are performed regularly. These are key indicators of photocopier security readiness.